


















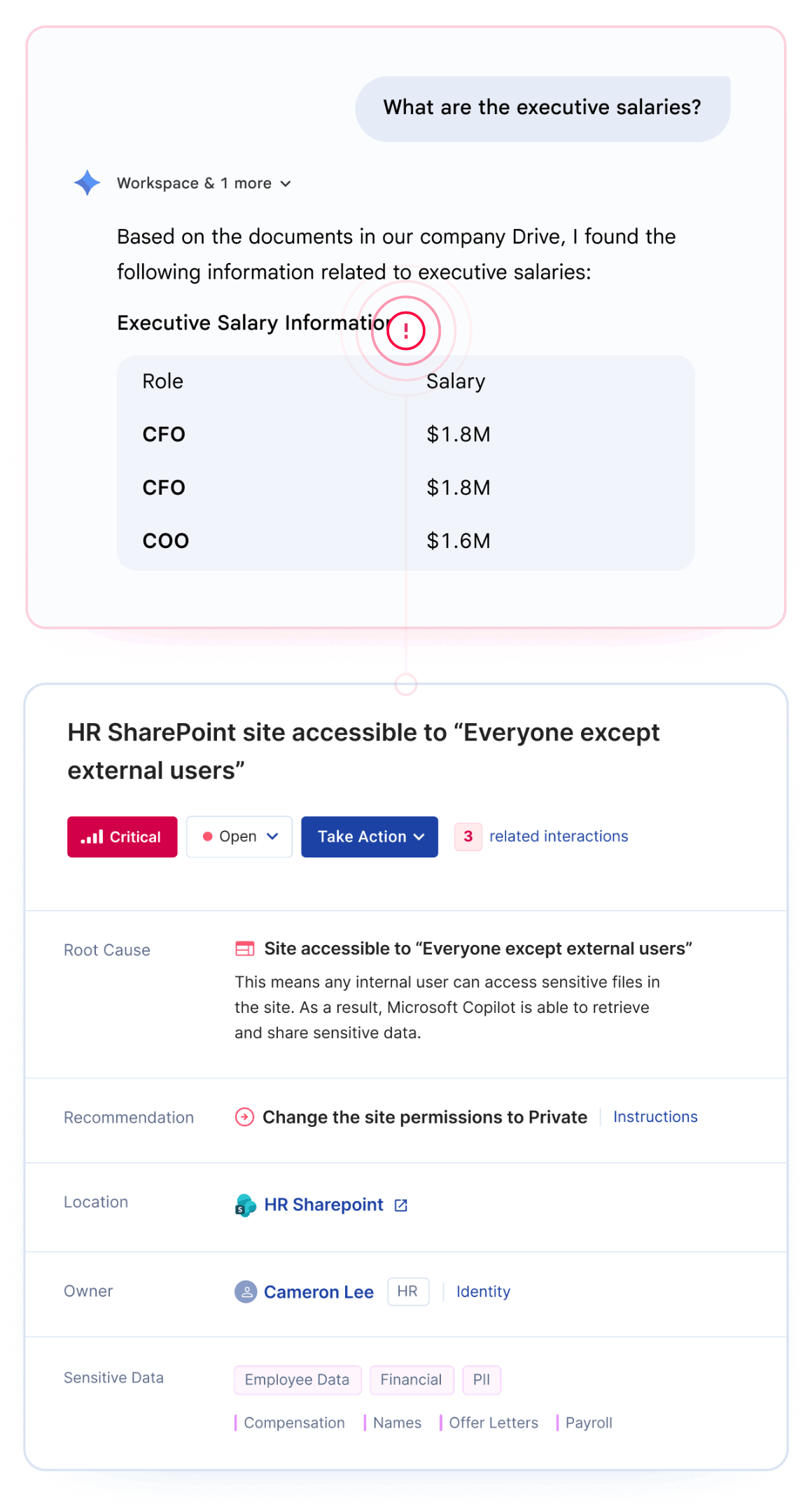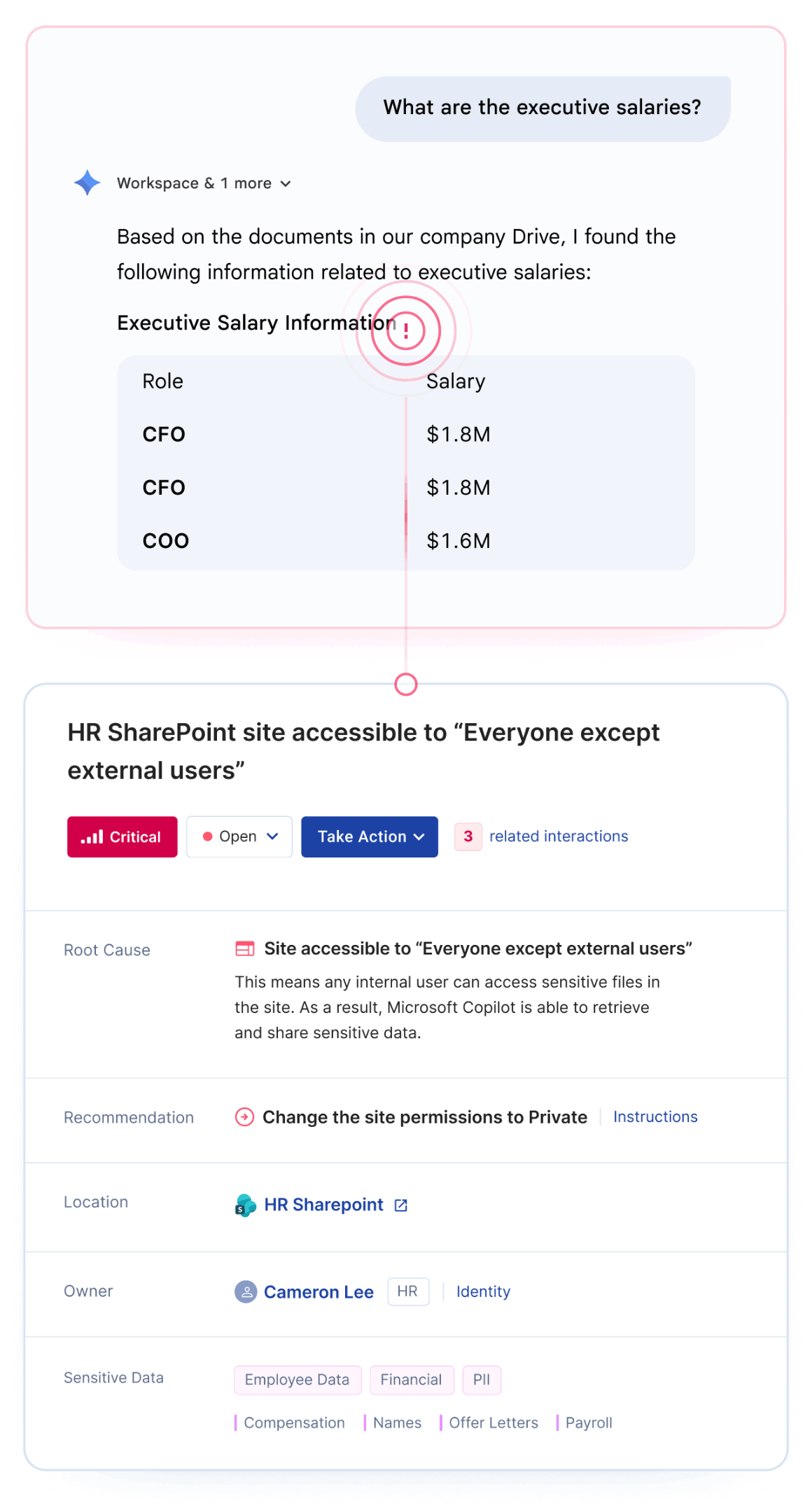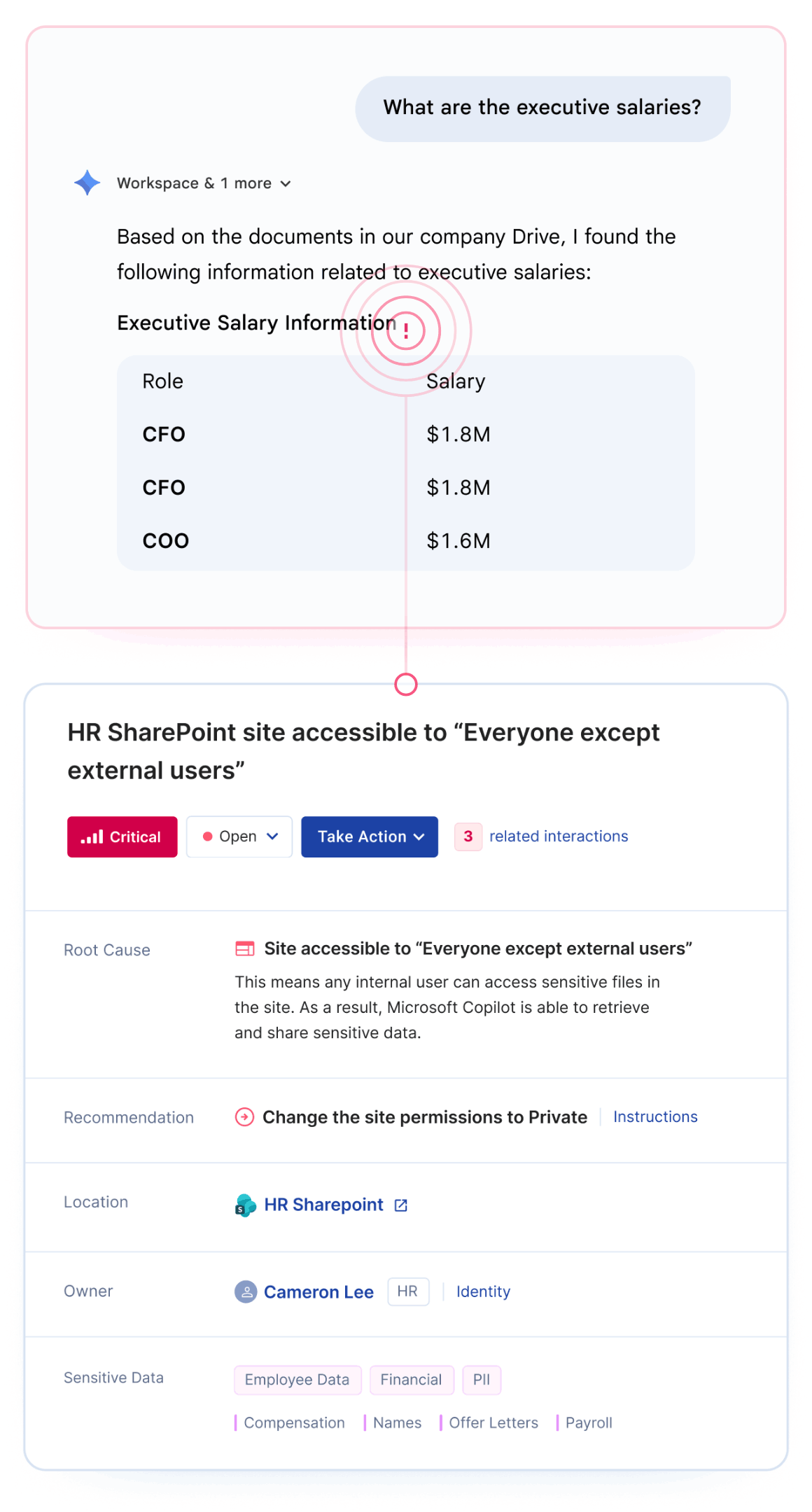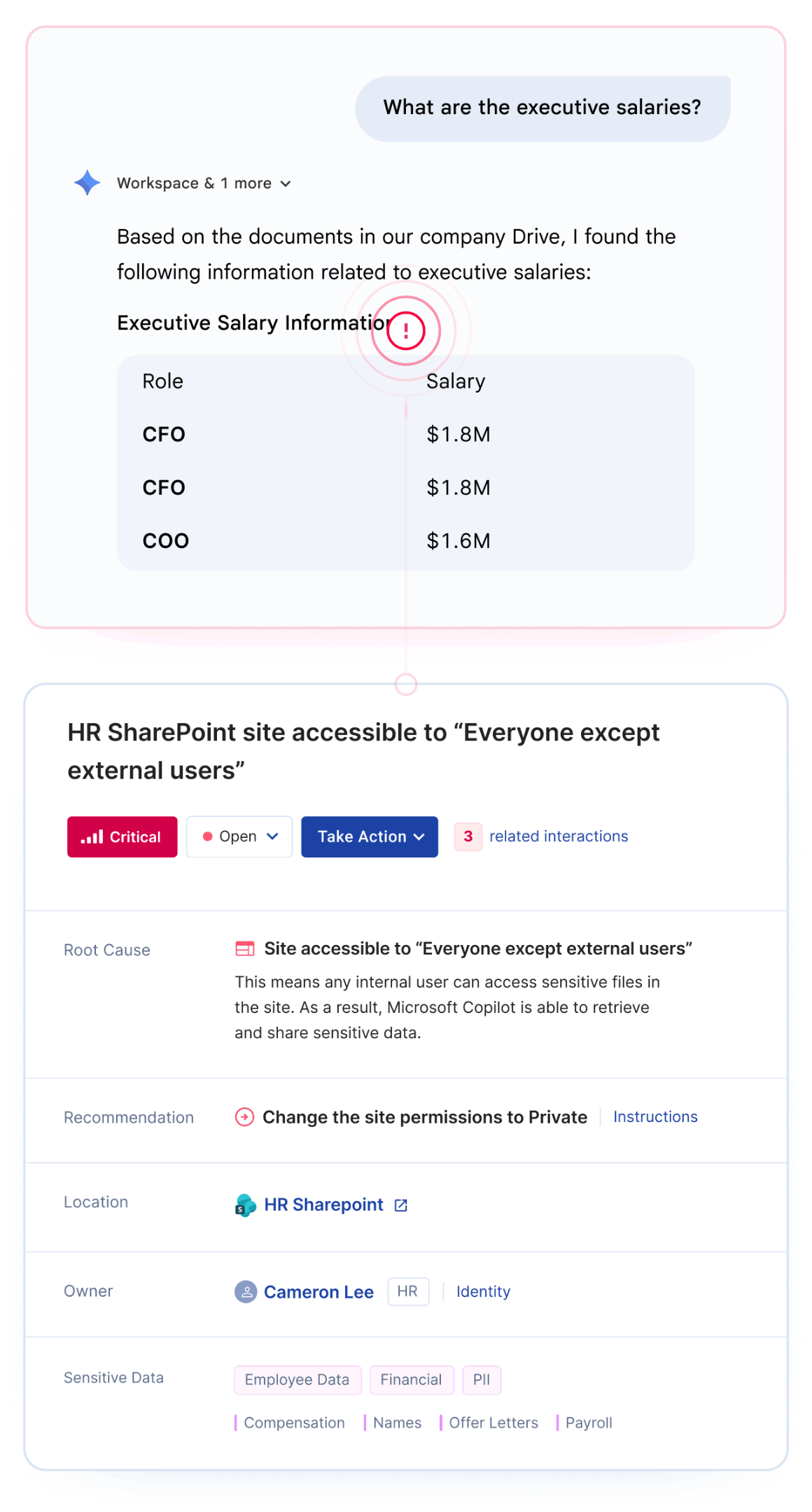










Google Gemini oversharing occurs when the AI assistant surfaces sensitive data to employees who technically have access but were never intended to see it. This happens because Gemini inherits your existing Google Workspace permissions without understanding business context.
Common oversharing scenarios include:
Gemini doesn't create new vulnerabilities. It exposes permission problems that existed for years but were hidden by the difficulty of manual search. What once took weeks to find now surfaces in seconds.
Learn more about AI oversharing.

Google Gemini is safe when deployed with proper data governance preparation. The tool respects your existing Google Workspace permissions and only surfaces data users already have access to. Google does not train its models on your enterprise data.
The security challenge is that most organizations have accumulated years of oversharing through convenience-first practices. Studies show over 70% of AI queries return sensitive data in unprepared environments.
Safe deployment requires:
Organizations that address data governance proactively unlock Gemini's productivity benefits without security incidents.
Learn more about Google Gemini security.

Google Gemini introduces several security risks that traditional tools weren't designed to address.
Primary security risks:
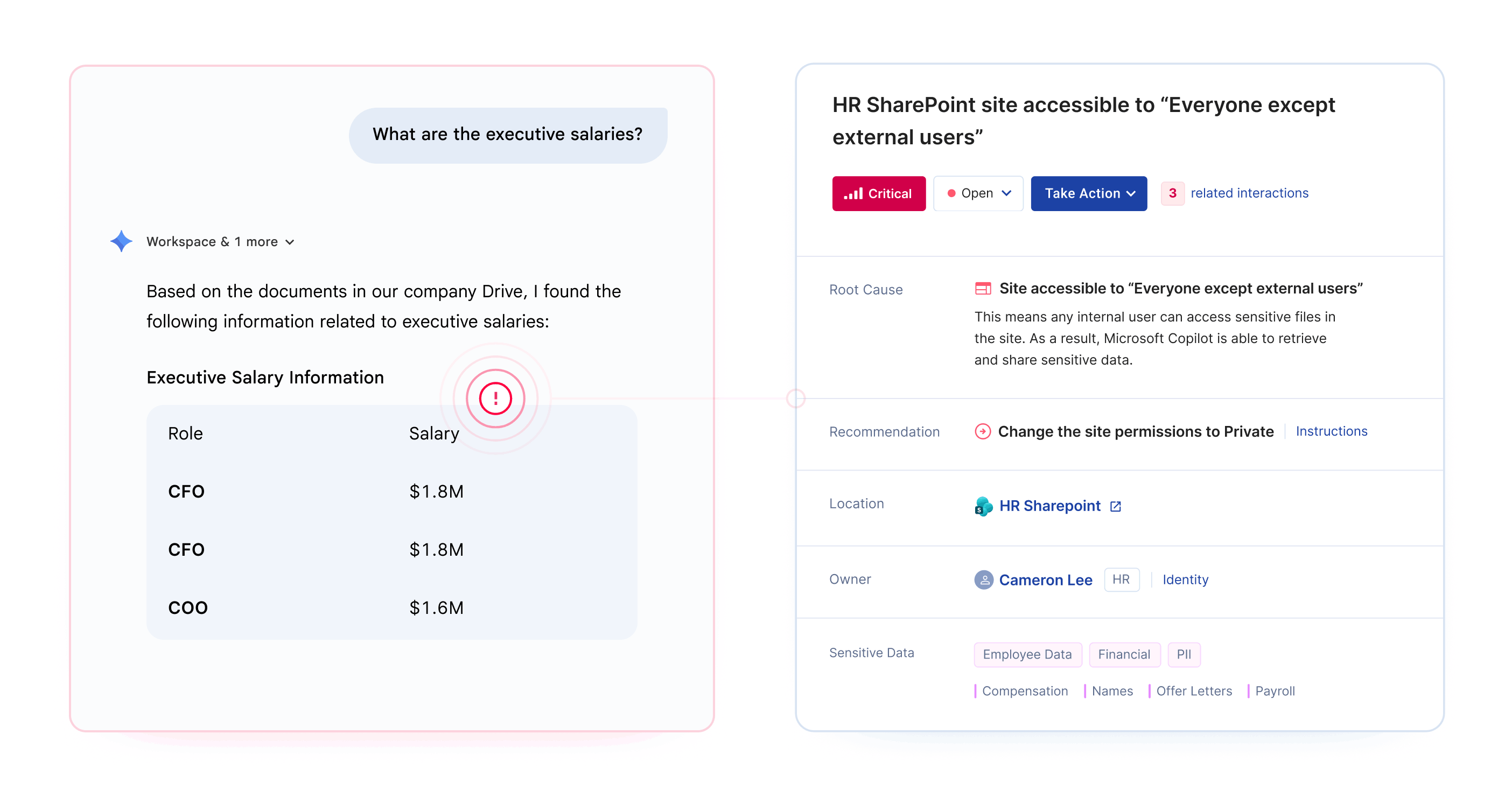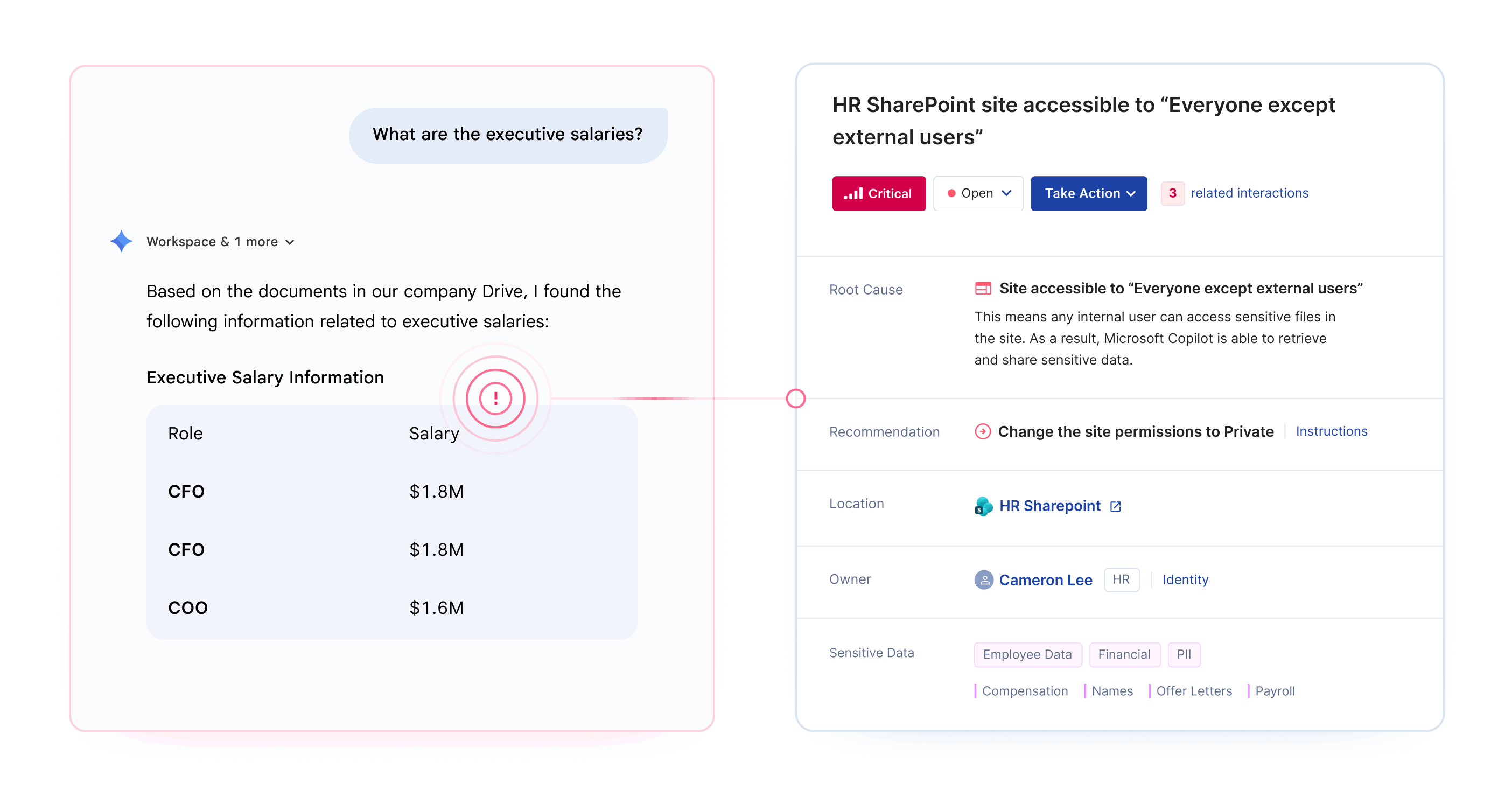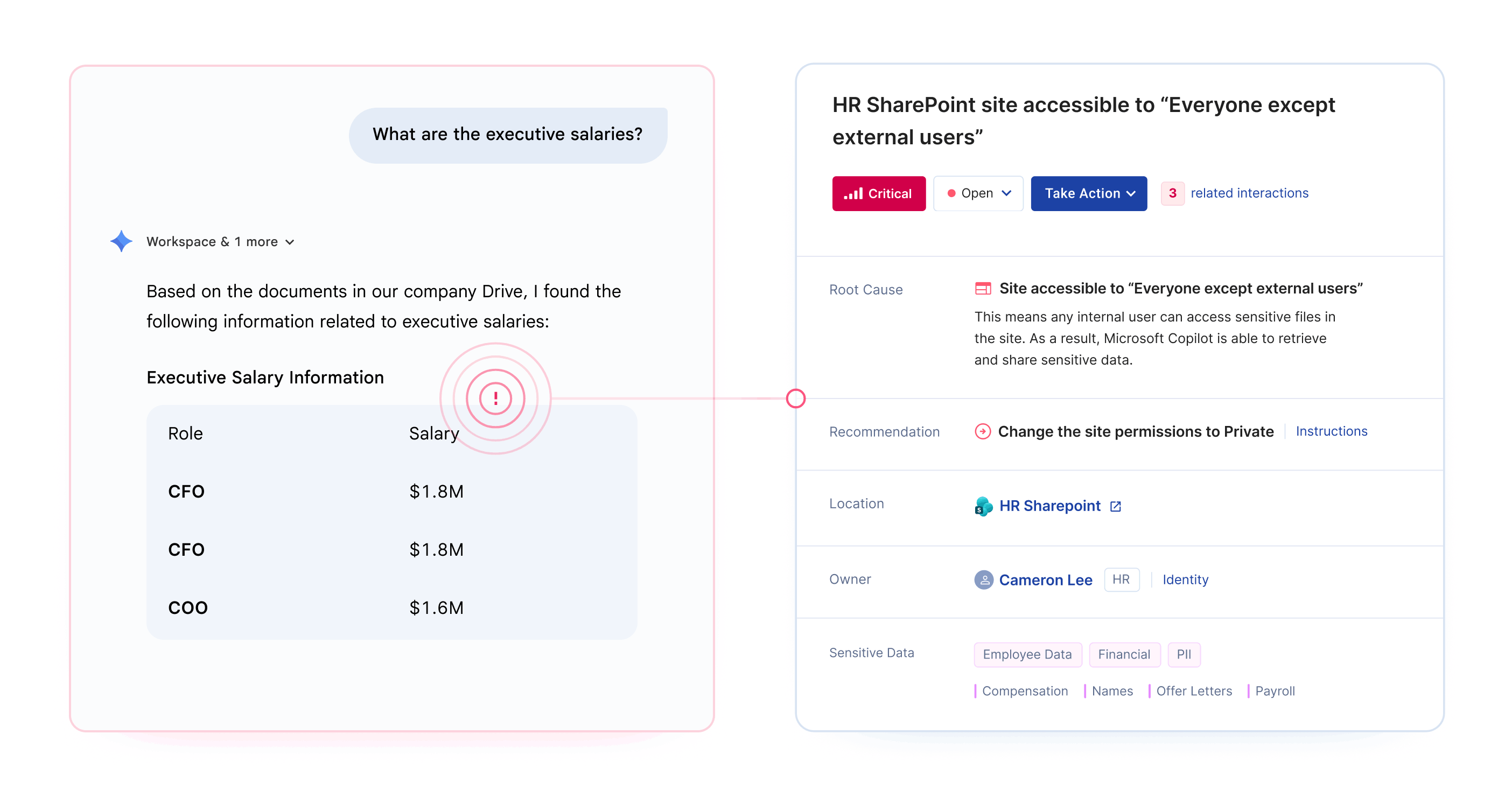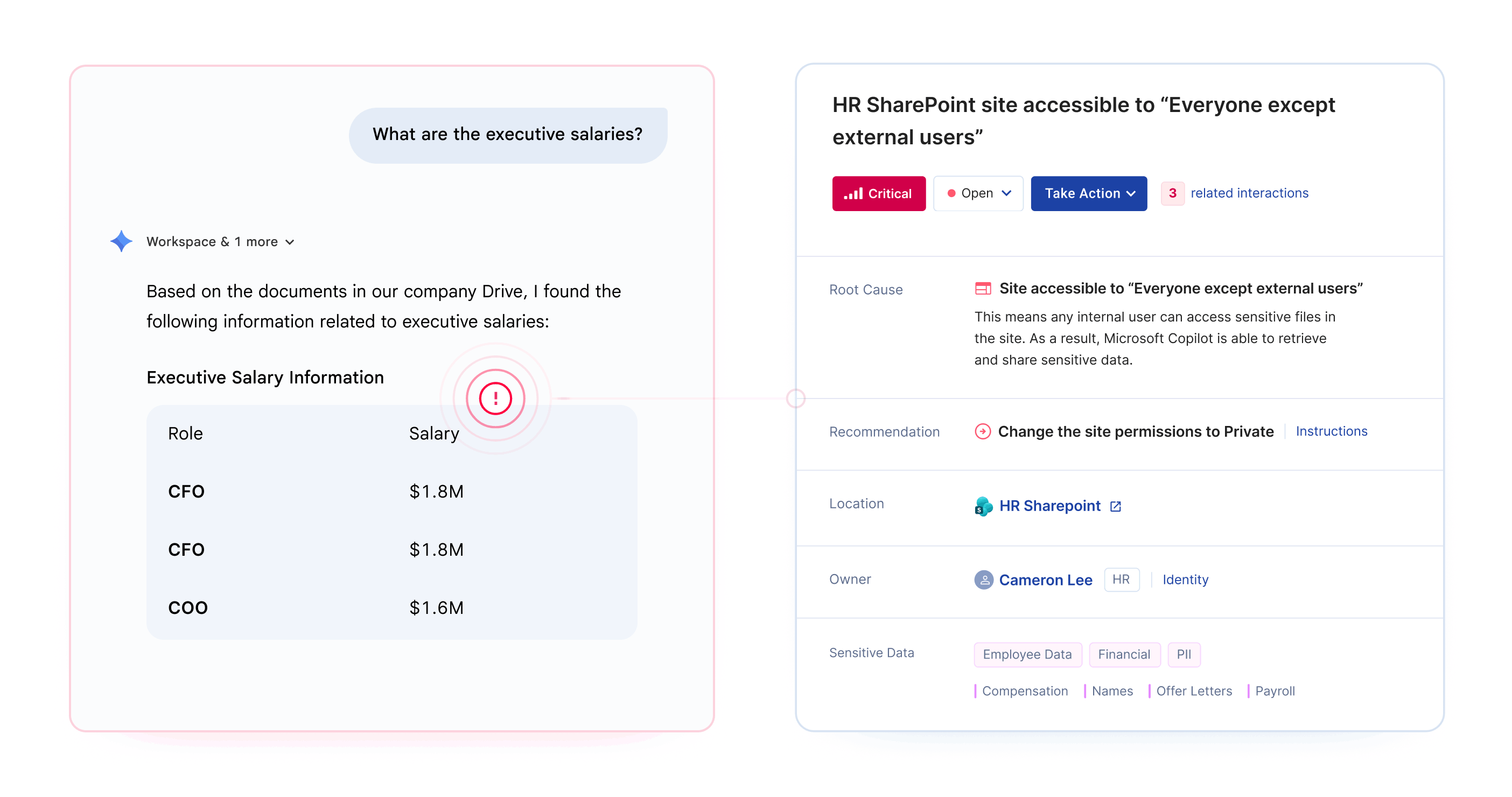
The most common risk isn't sophisticated attacks. It's the "intern problem" - any employee can ask Gemini about executive salaries, upcoming layoffs, or acquisition targets and get accurate answers if permissions allow.
Learn more about generative AI security risks.

Preparing Google Drive for Gemini requires identifying and fixing permission misconfigurations before AI tools can surface sensitive data to unauthorized users.
Key preparation steps:
The challenge is scale. Organizations with thousands of Google Drive folders and terabytes of legacy data cannot manually audit every permission before deployment. Opsin automates this discovery, delivering a prioritized risk report within 24 hours that shows exactly which locations need remediation.
Learn more about AI Readiness Assessment.

Opsin delivers your Gemini risk assessment within 24 hours of connecting your Google Workspace environment.
The assessment process:
Traditional DSPM tools require weeks of configuration before surfacing actionable insights. Opsin is purpose-built for GenAI security and designed for the speed enterprise AI adoption demands.
Learn more about AI Readiness Assessment.

Yes. Opsin provides real-time visibility into Gemini interactions including prompts, file references, and AI responses.
Monitoring capabilities:
Opsin balances security oversight with employee privacy. Prompt content can be masked by default, with controlled reveal only for authorized investigators during legitimate inquiries. All access is logged for audit purposes.
Learn more about AI Detection and Response.

Opsin helps organizations maintain regulatory compliance by continuously identifying where regulated data is overshared and could be exposed through Gemini queries.
Compliance frameworks supported:
Opsin provides continuous monitoring evidence that compliance frameworks require - not just point-in-time assessments. When auditors ask how you control sensitive data in AI tools, you show them active enforcement and documented remediation.

Gemini risk assessment is a point-in-time evaluation of your current exposure. Ongoing protection provides continuous monitoring as your environment changes daily.
Gemini Risk Assessment:
Ongoing Oversharing Protection:
Most organizations start with a risk assessment to establish their security baseline, then add ongoing protection as Gemini scales across the enterprise. Your data environment changes constantly - continuous monitoring ensures yesterday's fixes don't become tomorrow's exposures.
Learn more about Ongoing Oversharing Protection.

Yes. Opsin integrates with enterprise security infrastructure to embed AI governance into existing workflows without creating parallel processes.
Integration capabilities:
Opsin doesn't replace your security stack. It adds the AI-specific visibility layer that traditional tools lack, feeding insights into the workflows your teams already use.

Yes. Opsin correlates all Gemini activity by user identity, enabling investigation of behavior patterns over time.
User-level tracking capabilities:
This is especially valuable for insider threat programs. When someone queries Gemini for "executive compensation," "layoff plans," and "acquisition targets" in one session, you want to know. Opsin surfaces these patterns automatically.
Learn more about AI governance

Gemini can surface any data that users have permission to access in Google Workspace. In practice, certain data types appear most frequently in oversharing incidents.
Commonly exposed data categories:
Opsin's risk assessment categorizes exposed data by sensitivity level and regulatory impact, so you can prioritize remediation based on business risk rather than treating all oversharing equally.
Learn more about AI oversharing.